first time poster, hope im not posting something too catastrophically bad
It’s 2023. TLS 1.0 is considered outdated and no longer allowed by default in the Linux desktop (and rightfully so).
Unfortunately, not every sysadmin is living in the same year as us. Today, I had to connect to my school’s institutional network.
Seems pretty simple right? Just a simple wpa-enterprise connection.
Wrong. For some inexplicable reason, phase 1 auth is still done entirely with TLS 1.0. Windows, Android and iOS are still accepting a TLS version this old, but that’s not the case with Fedora, preventing a connection from being made.
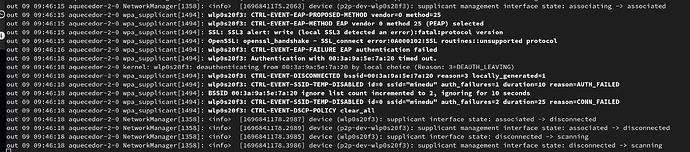
The issue is pretty simple. The authentication fails, but the user interface handles the failure generically; it retries three times, then (sometimes) prompts the user to provide their credentials again. This behaviour is pretty bad because it makes the user think that their credentials are wrong, instead of letting them know what the actual issue is.
It’s possible to identify the issue by checking the system’s logs, but you need to know what you’re looking for. (SSL unsupported protocol)
You can then manually configure NetworkManager to accept TLS 1.0 (just on the offending network) with the nmcli utility.
Although the issue can be fixed, the way you go around it is very user unfriendly, especially when you consider that users on other operating systems are able to connect without making any changes to the configuration.
Some options, including allowed TLS protocols, are not exposed graphically and are generally only editable via nmcli, and, in some cases, editing the connection’s configuration via settings actually resets these flags, requiring another visit to nmcli.
In the short term, I believe that the user should simply be prompted when their connection is using an incompatible TLS protocol. Even if no way to rectify the issue graphically is given, simply being aware of what you’re actually supposed to be looking at would be extremely helpful.
Long-term, the number of network options available graphically in settings should be increased. I believe that a simple “Allow legacy encryption standards (Unsafe)” toggle would suffice, but there’s probably a smarter way to do it in terms of UX.